Our technology driven world has expanded the term virus beyond a biological agent that replicates in the human body to malicious software invading a computer or device. Ransomware is one of many such viruses that can take different forms. As the term alludes, ransomware takes a hostage and demands payment of a ransom. In its essence, the virus blocks a user’s access to a device or files until a ransom is paid.
Imagine a situation where all client files are inaccessible. This is not farfetched as ransomware can encrypt or conceal data not only on your workstation, but is smart enough to travel across your network to corrupt files - both mapped and unmapped in network drives. One infected user can bring to halt an entire department or organization. According to Dimension Data, attacks increased by 350% in 2017.
Ransomware typically has a one-week deadline which, once passed, causes the ransom to increase. Once files are encrypted, the hackers will display a screen or webpage with payment instruction in order to unlock the files. Ransom payments usually start in the range of USD300-500 and once the deadline has passed payment will likely increase to over USD1,000. An average attack may cost a business approximately USD2,500.
Paying the ransom invariably involves paying a form of e-currency (cryptocurrency) like Bitcoin, also called BTC. Once the hackers verify payment, they provide a “decryptor” software, and the computer or device starts the arduous process of decrypting all of the files.
Some Facts about Ransomware.
In 2017, the WannaCry variant of ransomware become the most widespread attack covering more than 70 countries. Before, the most widely known variant was CryptoLocker which made USD27 million in September 2013, followed by the variant CryptoWall, which made USD325 million over 18 months, half of that in the United States of America.
- With a 29 percent prevalence, Cybersecurity Ventures ranks ransomware as the top malware, a software designed to disrupt a system in Europe Middle East and Africa (EMEA).
- According to Cybersecurity Ventures, in 2017 ransomware damages reached USD5 billion.
- The principal sectors most vulnerable to ransomware attacks in EMEA are business and professional services directly followed by finance.
- At roughly USD1 million, Nayana, a South Korean based web hosting provider has to date made the largest ransomware payment.
- Typically, ransomware software uses RSA 2048 encryption, it would take about 6.4 quadrillion years for a desktop computer to crack an RSA key.
Am I Infected? What are the symptoms.
It’s fairly straightforward to find out if you are affected by a ransomware virus. The symptoms could be one of the following.
- You suddenly cannot open normal files and get errors such as the file is corrupted or has the wrong extension.
- You receive an alarming message to your desktop background with instructions on how to pay to unlock your files.
- You are notified your files are encrypted and warned if payment is not made by end the of the countdown, the ransom demand will increase.
- A window has opened to a ransomware program and you cannot close it.
- You see files in all directories with names such as HOW TO DECRYPT FILES.TXT or DECRYPT_INSTRUCTIONS.HTML.
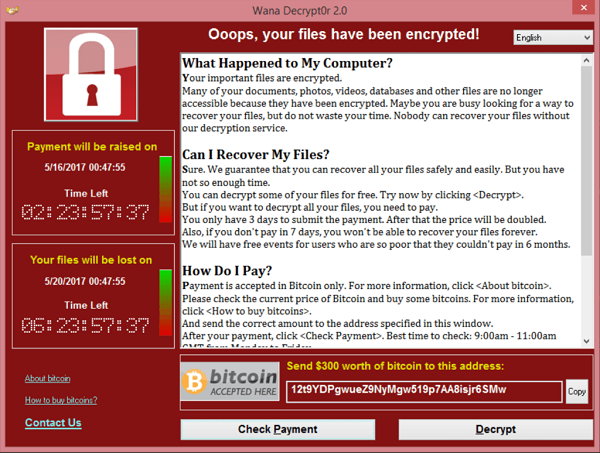
Source: Reuters, 2017 WannaCry Ransomware demand
Infection vectors. Common ransomware attack methods.
Email vector - the most common way ransomware is installed involves an email attachment disguised as a harmless file. Hackers will send a file with multiple extensions in an attempt to hide the true type of file you are receiving. A user will receive an email with a file attachment or a link to download software. If the user opens the file attachment or installs the software, this directly leads to a ransomware infection.
Drive-by-download – increasingly, infections happen through drive-by downloads, where visiting a compromised website with an old browser or software plug-in or an unpatched third-party application can infect a machine. The compromised website runs an exploit kit (EK) which checks for known vulnerabilities. Often, a hacker will discover a bug in a piece of software that can be exploited to allow the execution of malicious code. Once discovered, these are usually quickly caught and patched by the software vendor, but there is always a period of time where the software user is vulnerable.
Free software vector – another common way to infect a user’s machine is to offer a free version of a piece of software. Examples include “cracked” versions of expensive games or software, screensavers, free games, game modifications or “mods,” adult content, or bogus software advertised as a way to cheat in online games or get around a website’s paywall. In this case, a user downloads the file directly allowing hackers to bypass any firewall or email filter.
Four ways to protect against ransomware.
- Use the latest versions of software or operating systems, reduce risks and minimize network security gaps by not using unpatched (software that is no longer updated or repaired) or out-of-date software.
- Increase organizational awareness, employee must know they need to verify authenticity of email senders and their intension before opening an attachment or downloading software.
- Protect your network, invest in anti-ransomware security solutions, there are tools on that market that will analyse suspicious activity then scan or block malware.
- Be strategic, invest in your security infrastructure, have current data retention policies and backup your data to an external drive or a cloud-based system.